On February 18, SonicWall’s Capture Labs reported that Russian cybercriminal group CryptoBytes intensified its Russian ransomware attacks with an upgraded UxCryptor, exploiting leaked ransomware builders to target Windows systems worldwide.
Recent studies show CryptoBytes enhanced UxCryptor with advanced anti-analysis features to make it harder to detect their activities. A ransomware attack from Russia further complicate tracking and disabling the malware.
The gang also uses psychological pressure tactics by issuing threats and demanding ransoms via Telegram account with the handle name yes_u_are_hacked.
How UxCryptor Works
The Russia ransomware attack is multi-phased, beginning with three successive ransom screens written in Russian. A translated ransom message is dropped in the victim system directory, where it demands cryptocurrency payments.
- UxCryptor incapacitates the system by killing Windows Explorer via a forced taskkill command:
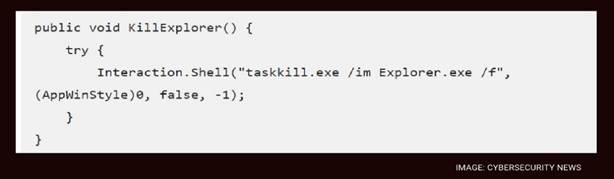
To evade analysis, the Russian hackers ransomware malware checks for sandbox environments and virtual machines before it runs. It also kills critical applications, like Discord, Skype, Zoom, and browsers, to hinder victims from communicating.
- UxCryptor modifies registry keys to deter recovery attempts:
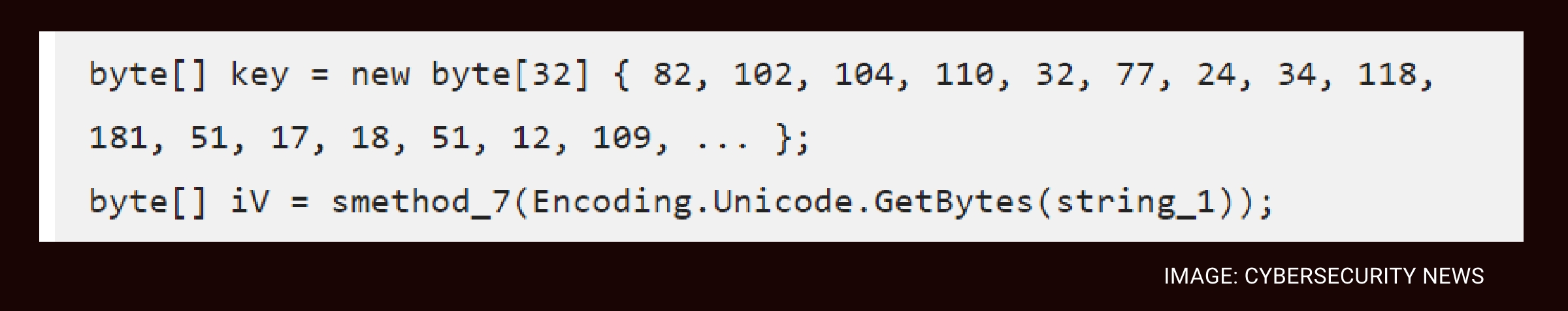
While some analyzed samples contained non-functional encryption code, operational implementations of UxCryptor use AES-256-CBC encryption with hardcoded keys to encrypt victims’ files. The encrypted files get a .ux-cryptobytes file extension.
Russian Ransomware New Threat to Businesses
SonicWall reports that CryptoBytes is escalating Russian ransomware attacks on small and medium-sized businesses (SMBs) in Eastern Europe. The Russian ransomware group managed to exploit leaked ransomware tools, indicating franchise-like model, where other cybercriminals to launch similar attacks easily.
Security experts advise organizations to patch Windows immediately, segment networks, and deploy advanced security solutions like SonicWall’s Capture ATP with Real-Time Deep Memory Inspection (RTDMI) to detect and block variants of UxCryptor. Up to February 2025, CryptoBytes continues to enhance the Russian ransomware, and it is a persistent threat in the emerging cybercrime landscape
Inside Telecom provides you with an extensive list of content covering all aspects of the tech industry. Keep an eye on our Cybersecurity sections to stay informed and up-to-date with our daily articles.