Hackers targeted around ten official websites in Italy on Saturday, including the websites of the Foreign Ministry and Milan's two airports.
Hacking
India's largest standalone health insurer, has been openly exposed via chatbots on the hacking Telegram messaging app.
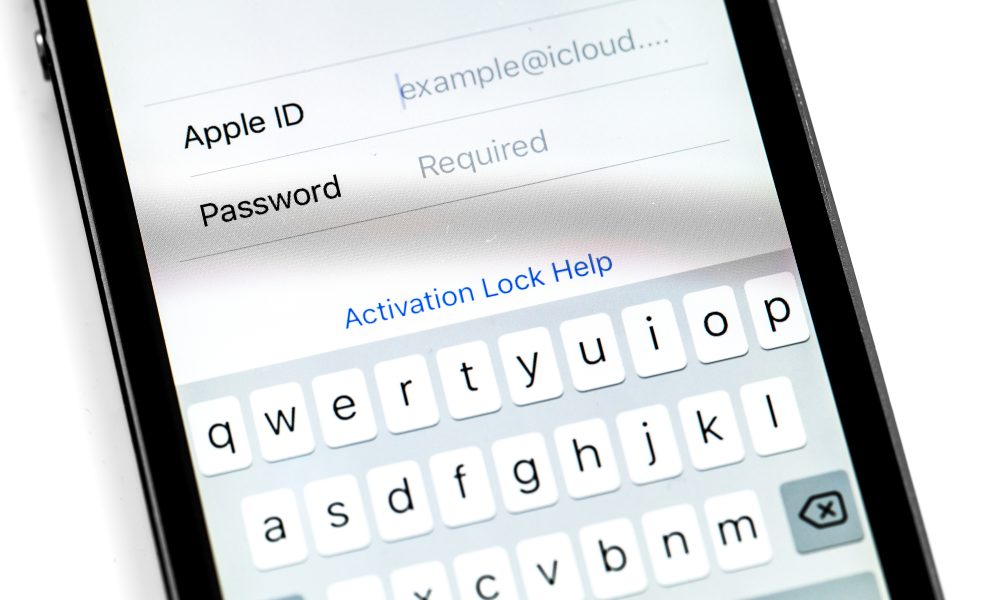
Important report reveals cybercriminals hacking Apple devices through users' Apple IDs, demanding devices protection from unauthorized access
China to increase protections against hacking in its key industrial sector as it aims to contain major risks by 2026.
The surveillance technology oversight project impacted global security, especially the Israeli-Palestinian war.
A group of keyboard warriors, known in the cyber space as "Cyber Toufan Operations," decided to hack the Israeli Ministry of Defense.
A Tesla hacker, known only as Green, recently a "congestion fee" for charging beyond 80% at busy Supercharger locations.
The dropbox data breach that recently took place highlighted prior security breaches. The passwords and data compromised come within an extensive list of primarily exposed credentials. It seems like dropbox is a frequent target for hackers. Dropbox might be considered negligent, but is that the case? Let us reflect further. How Did it Happen Like […]
Australian telecom giant, Optus, fell victim to a hack. Exposing nearly 2.1 million of its current and previous clients suffered a data leak of their personal and critical information. With at least one form of their identification number leaked due to the breach. Optus infotech has already started its quest to try and save itself. […]
Uber Technologies Inc on Friday accepted responsibility for covering up a 2016 data breach that affected 57 million passengers and drivers, as part of a settlement with U.S. prosecutors to avoid criminal charges. In entering a non-prosecution agreement, Uber admitted that its personnel failed to report the November 2016 hacking to the U.S. Federal Trade […]