In this digital age, telecommunication has become an integral part of our lives. People are constantly worried about their data privacy when they access a program or smartphone. Cyber-attacks can happen to anyone using technology, including telecommunication companies. Cybercriminals are developing new and sophisticated methods to breach data security and steal sensitive information as technology […]
Search results for "passwords"
As technology experts and enthusiasts, you know something serious is going down in European Union (EU) when four of its telecom giants join hands to develop the advertising venture of a lifetime. Germany’s Deutsche Telekom, France’s Orange, Spain’s Telefónica, and the UK’s Vodafone dominate the telecom industry in their respective countries. Deutsche Telekom, for example, […]
In the last few years, digital banking has become increasingly popular due to the convenience it offers consumers. It allows you to access your financial information and perform various transactions anytime, anywhere, saving you the hassle of visiting a branch and waiting in long queues. Digital Banking’s Various Uses Digital banking refers to the use […]
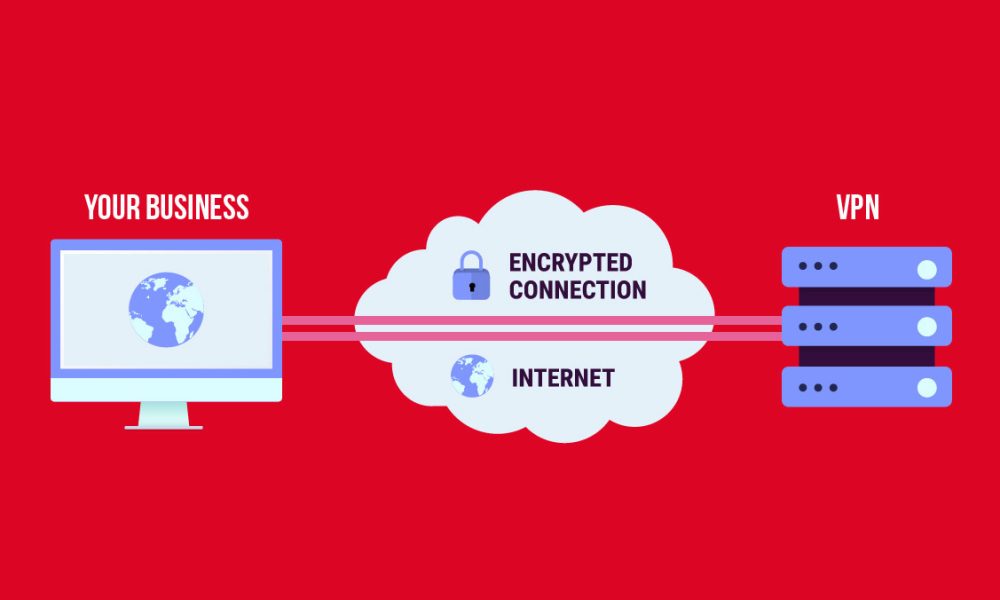
Security for personal data and innovations is vital when starting your own online business. In this scenario, you’ll need to be able to utilize a variety of strategies to maintain cybersecurity, train your staff, and install a reputable VPN. In addition to assisting, you with cybersecurity, a VPN for businesses may provide you access to […]
With billions of worldwide Fifa World Cup viewers, it is a gold mine for hackers and malicious actors to exploit. Football fans aren’t the only ones tuned in to see some of the world’s top players fight for the title of 2022 champions. These eye-catching events also pique the interest of cyber threat actors with […]
The widespread use of the Internet nowadays results in severe leaks of private information. Security breaches and hacker attacks have become commonplace, and numerous frauds and scams online are our present-day reality. Even if you do not feel endangered or extremely worried about your online security, there are certain factors to take into consideration when […]
Cyberattacks’ volume and sophistication level have continuously increased over the last few years. A more comprehensive portion of the economy is now potentially a target due to the digitalization of business. The Covid-19 pandemic caused more people to work from home, catalyzing the process. The attack surface is expanding as the number of connected devices […]
In our current era, data and information are becoming an increasingly crucial element in our daily life. Be it as an individual or a customer, your data is vital. The right to privacy is essential for you to understand and protect. IT can gain visibility into all your data infrastructure within an evolving technology landscape. […]
Many startups might not place cybersecurity at the top of their priority list, or take the taime to put together a strategy, but that’s a significant mistake they might come to regret once it’s too late. Building a culture of cyber security and taking the required steps, such as setting up security software and using […]
Microsoft released Windows 11, their latest operating system (OS), a year ago. In September 2022, however, they introduced a new free update, Windows 11 22h2. This update constitutes the first significant update of the new generation of Windows. It introduced a new set of features, enhancing security, productivity, and overall user experience. The new update […]