The further technology goes, the deeper it sinks into your home. The IoT (Internet of Things) smart home applications automate everything in your house, from lighting to locks. The first proper home automation device, ECHO IV, was invented in 1966 by Westinghouse engineer Jim Sutherland and It was all uphill from there. IoT Smart Home […]
Security
Amazon Simple Storage Service, S3, is a cloud object storage service offering world-class services. Data availability, security, and performance. Companies from various scales can use Amazon S3 to store and keep their data safe. Amazon S3 offers management features allowing you to optimize and organize your data. Many myths have been formulated, so which of […]
One of the greatest rates of regional digital adoption may be seen in the United Arab Emirate (UAE), but consequently, has seen a proportional increase of cybercrime in Dubai and the surrounding areas. The World Digital Report 2021 provided information on 43 nations’ web-based lifestyles in 2020, including the UAE. In the past year, UAE […]
Live blockchains are growing daily at an ever-growing pace. As of our present day, there are more than 10 000 active Blockchain-based cryptocurrencies. With such a presence, having the right knowledge base has never been more valuable as this decentralized technology becomes more and more embedded into global establishments. So, what are the pros and cons […]
During the past decade, password leaks and data breaches have hit companies, such as Facebook, Equifax, Home Depot, Marriott, Yahoo, Target, and countless others, which requires security of data to be present. Hackers leaked information and data on at least one of the online accounts. To know which of the accounts was compromised? Search […]
With every rising technology and telecom innovation comes new threats to infrastructure and user’s information security, the most common among them being ransomware. These perils are becoming more common as criminal groups and hackers continually develop methods to prevent or defeat the implemented security measures. The telecom sector is seen as one of the most […]
A consortium of cybersecurity specialists launched on Tuesday an initiative to encourage companies to implement preventive security measures to end abusive online behavior experienced by workers. Respect In Security, launched by Lisa Forte from Red Goat Cyber Security and Trend Micro’s Rik Ferguson on July 14 on Twitter, is a long overdue plan that focuses […]
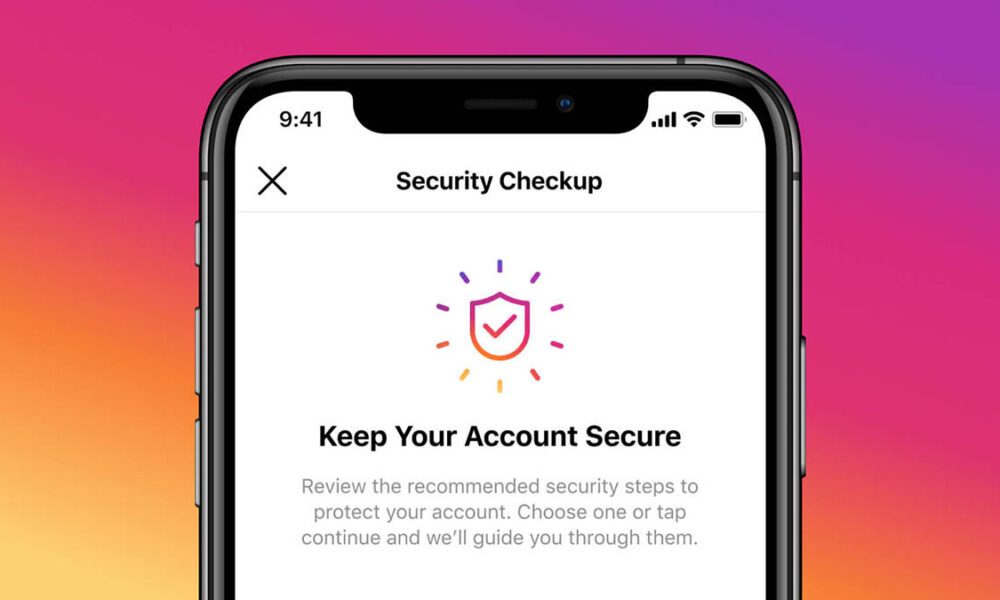
Instagram announced on Tuesday a security feature that would enable its users to help recover their hacked accounts. The Facebook owned platform revealed the new tool called “Security Checkup” in a blog post to guide its users, whose accounts may have been hacked, through the steps needed to secure them. Users through this feature will undergo four major steps: after checking their login activity, they will be asked to review their profile information, followed by a confirmation […]
BGP (Border Gateway Protocol) is a fundamental support system of the internet. It is designed to exchange routing and reachability info among autonomous systems on the internet. This important tool is essential for network stability. Security vulnerabilities of BGP can lead to heightened attack risks that can impact our businesses and many aspects of society. […]