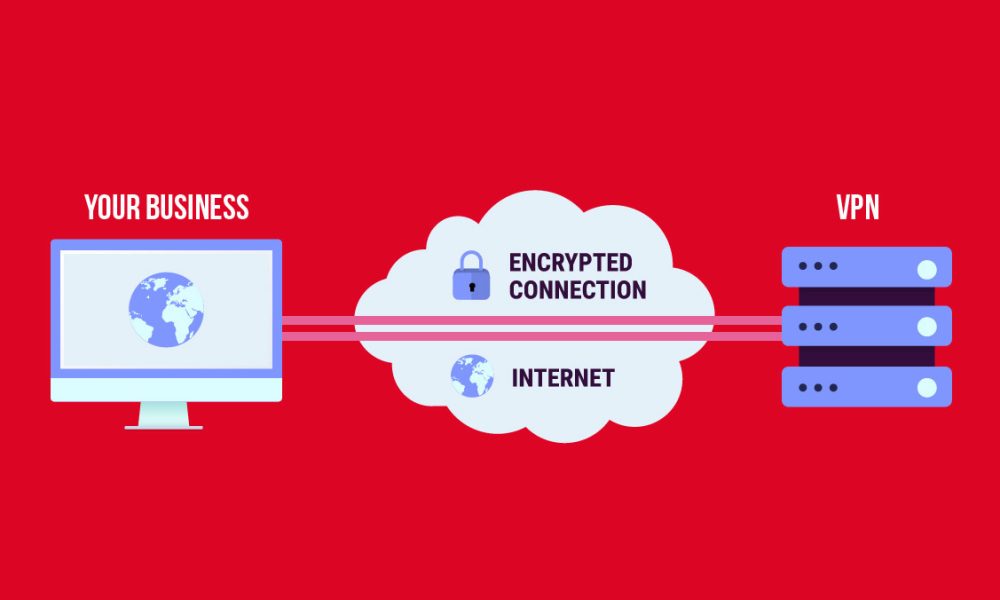
Security for personal data and innovations is vital when starting your own online business. In this scenario, you’ll need to be able to utilize a variety of strategies to maintain cybersecurity, train your staff, and install a reputable VPN. In addition to assisting, you with cybersecurity, a VPN for businesses may provide you access to […]
Cybersecurity
China began enforcing its most recent cybersecurity regulations,”MLPS 2.0,” which mandate that businesses install government-approved network equipment and make their networks transparent to Chinese government authorities. The Chinese Ministry of Public Security will now receive cybersecurity strategy reports from all companies operating in China. They will be permitted to monitor their secure networks. According to […]
Dual transformation and industry restructuring are necessary to restore the trust and support of customers. To stop the commoditization of the network, the telecom sector will need to alter its primary business. They will need to develop a universally applicable solution for all clients. They must comprehend why the network needs to be restructured to […]
With the world’s accelerated industrial and technological revolution, countries are increasingly adopting intelligent digital solutions to fortify their frameworks, be it economic, sustainable, or even security. With the world’s interconnection, the fusion of development is amplifying, and with this upsurge, the global embrace of technological means has reached new pinnacles. Technologies such as Artificial Intelligence […]
Popular short-video app TikTok is offering to operate more of its business at arm’s length and subject it to outside scrutiny as it tries to convince the U.S. government to allow it to remain under the ownership of Chinese technology company ByteDance, according to people familiar with the matter. TikTok has been seeking to assure […]
When it comes to cybersecurity, telcos are faced with a wide range of diversity and complexity, including distributed and cloud RAN, Edge and Cloud Core, enterprise and subscriber devices, gateways, hubs, set-top boxes, multi-capacity routers, switches, base transceiver stations, femtocells, and 5G edge gateways. Hacker groups, APT groups and clusters, and malware creators frequently target […]
Cybersecurity started in the 1980s after Morris created the first worm, a program capable of moving through a network and leaving behind a trail. Ever since then, cybercrime has only evolved to become the digital era’s biggest problem. Subsequently, companies and individuals alike now need to put up exceptional cyber defenses and put down protocols […]
With billions of worldwide Fifa World Cup viewers, it is a gold mine for hackers and malicious actors to exploit. Football fans aren’t the only ones tuned in to see some of the world’s top players fight for the title of 2022 champions. These eye-catching events also pique the interest of cyber threat actors with […]
The widespread use of the Internet nowadays results in severe leaks of private information. Security breaches and hacker attacks have become commonplace, and numerous frauds and scams online are our present-day reality. Even if you do not feel endangered or extremely worried about your online security, there are certain factors to take into consideration when […]
Cyberattacks’ volume and sophistication level have continuously increased over the last few years. A more comprehensive portion of the economy is now potentially a target due to the digitalization of business. The Covid-19 pandemic caused more people to work from home, catalyzing the process. The attack surface is expanding as the number of connected devices […]