Crown Resorts said on Monday a ransomware group had contacted the company, claiming that they had gained access to some files related to Australia’s biggest casino operator following a data breach at a file transfer service GoAnywhere. “We were recently contacted by a ransomware group who claimed they have illegally obtained a limited number of […]
Search results for "security breach"
Deep in the heart of modern business technology, there lies a hard choice between two different types of 5G networks: private and public. These networks have been shrouded in secrecy and misunderstood by many. However, in today’s rapidly changing world, it is essential to understand the key differences between these two types of networks, especially […]
In the digital age, telcos have become the natural partner of many industries, including the metaverse. Our interest in this article lies in the fintech sector. In a previous article, we stated why telecom companies are attractive to the fintech industries. Through such a partnership, these two industries hope to expand their services to the […]
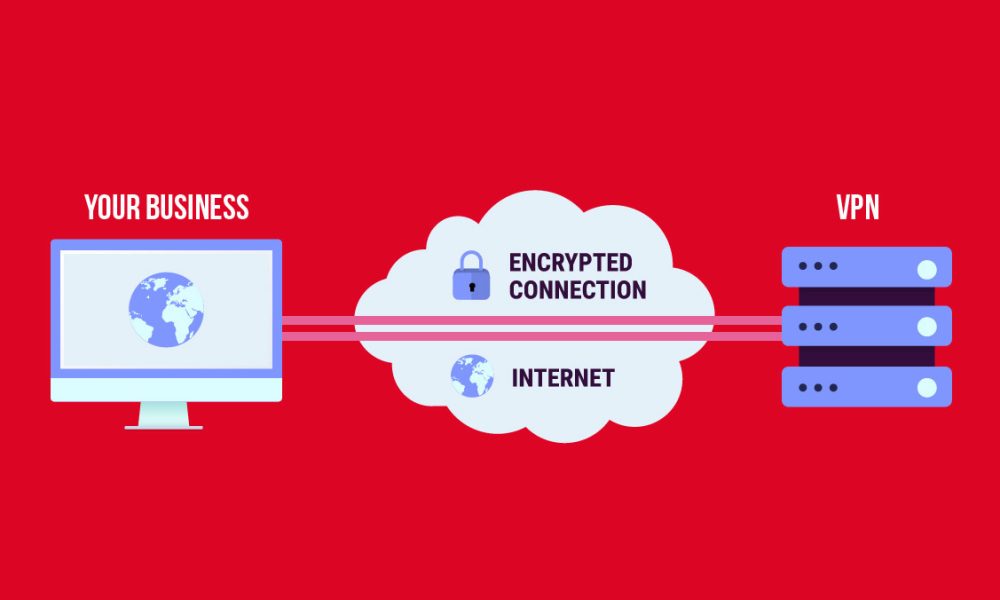
Security for personal data and innovations is vital when starting your own online business. In this scenario, you’ll need to be able to utilize a variety of strategies to maintain cybersecurity, train your staff, and install a reputable VPN. In addition to assisting, you with cybersecurity, a VPN for businesses may provide you access to […]
Cyberattacks’ volume and sophistication level have continuously increased over the last few years. A more comprehensive portion of the economy is now potentially a target due to the digitalization of business. The Covid-19 pandemic caused more people to work from home, catalyzing the process. The attack surface is expanding as the number of connected devices […]
Blockchain Revolutionizing Data Sharing In the era of big data and artificial intelligence, sharing data is inevitable and even a prerequisite for business innovations and scientific breakthroughs. Yet, concern over data privacy is growing by the day as we lack of secure data-sharing solutions. Meanwhile, decentralized data-sharing platforms, mainly Blockchain, are being leveraged to add […]
We are all well aware of the troubles opening a fishy link can lead us to. Luring users to click on a given link has been of one the well-known techniques to get access to the device, install virus and malware or even go as far as creating a full ransomware attack. To protect your […]
The telecommunications industry is not immune from the political tensions and the war of attrition that has been reigning between China and the USA and other European countries for some time now. The emergence of Chinese vendor and original equipment manufacturer Huawei as a serious competitor to other vendors and manufacturers has been a notable […]
Data is undoubtedly the central player in today’s business world. The different markets have reached a level of competitiveness that companies have been looking for the killer idea or even the best understanding of the market that will provide it with a competitive edge. Artificial intelligence (AI) has become an integral component in the operations […]
For the police, the use of facial technology in a technologically accelerated world is nothing but a means to optimize their internal operations to deliver a more safeguarded environment, conduct faster investigations, and catch criminals. But for the public, the police use of facial recognition is a cause of concern in terms of a potential […]